
When SD-WANs very first started to be talked about, the focus of the discussion was on the possible cost savings that would arise from integrating more cost-efficient broadband connectivity into the WAN. Decreasing expense is clearly an essential objective, but attaining that goal is just significant if the WAN is likewise offering all the requisite functionality. This blog site will discuss the significance of WAN performance such as security and the capability to efficiently support cloud computing. This blog will also recognize the key attributes of a secure SD-WAN.
Needed WAN Functionality
The performance that WANs should offer was recognized in the 2018 Guide to WAN Architecture and Style. That guide presented the results of a survey in which the participants were presented with fifteen factors and asked to select the top 3 aspects that would likely have one of the most impact on their WAN over the next twelve months. The factors that were the most crucial are displayed in Figure 1.
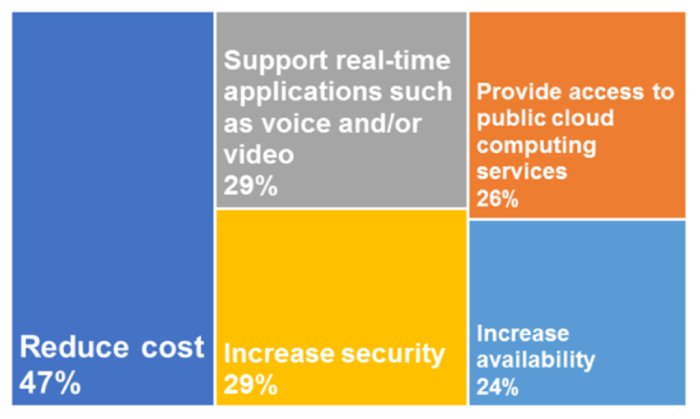
Figure 1: Top 5 Aspects impacting WAN
As might be anticipated, minimizing cost remains the primary factor impacting the WAN. Figure 1 shows that the WAN must likewise offer a range of performance, consisting of offering access to public cloud computing services and Figure 1 likewise shows that no functionality is more important than increasing security.The 2018 Guide
to WAN Architecture and Style also highlighted that the requirement to support a variety of performance is affecting how business network IT organizations assess SD-WAN solutions. The guide provided the outcomes of a study in which the respondents were asked to indicate their level of interest in obtaining SD-WAN options that supported L4-L7 performance. By a large margin, the most common reaction was that the solution they adopt must support a large variety of security and optimization functionality.The Components of a Secure SD-WAN Offering conventional security functionality in a much easier and more effective way is both part of the challenge and part of the opportunity that is associated with an SD-WAN. In a traditional WAN it’s technically possible to manually script and manage granular security policies. The amount of time and work that this approach needs implies that it isn’t feasible for any however the smallest of networks. In a secure SD-WAN it should be simple for network administrators to centrally specify and manage granular security policies and to set up and handle safe and secure end-to-end zones throughout any mix of users, application groups and virtual overlays.In reaction to the ever-increasing elegance of security attacks, lots of companies
are trying to embrace both a micro-segmented network security architecture and a zero-trust method whereby they confirm whatever inside or beyond their networks before granting access. Executing network segmentation within a LAN is quickly done utilizing VLANs. In a traditional router-centric WAN, segmenting the WAN has actually been a manually-intensive, device-by-device task that required the usage of arcane CLIs. In a safe SD-WAN it must be possible for network administrators to rapidly and easily manage and handle granular zone-based security policies, to segment and assign applications to zones and to segment end-to-end zones across the LAN and WAN. To enhance control and increase availability, network administrators need to likewise be able to define a transport geography and fail-over policies for each zone.There is a huge variety of security performance offered in the market including next generation firewall programs, intrusion detection and avoidance, Web entrances, anti-malware, authentication and authorization, danger intelligence and behavioral analytics. In the existing environment this functionality can be executed in a variety of areas. For example, in some instances, security performance is executed on site. In a big and growing number of circumstances security performance is carried out offsite, either in the cloud or at an enterprise’s regional hub or data. The truth that security functionality can be located in a range of places implies that network organizations need to pick an SD-WAN option that can determine and classify application and web traffic utilizing just the very first package of the circulation and can instantly guide traffic based on centrally defined security policies.It isn’t reasonable to expect that any SD-WAN provider will supply all the essential security functionality. A better approach is to search for SD-WAN providers that have a broad variety of security partners that provide the complete variety of leading edge security functionality. However, having a broad variety of partners is just reliable if the SD-WAN service supports the standards-based IPsec WAN connectivity that is required to integrate with cloud-based security services. The solution needs to also offer a seamless way to service chain all the proper security functionality regardless of where that functionality is implemented.Conclusions All companies, whether they have embraced a cloud-first approach, are making increased usage of cloud services. This fact integrated with the big and growing value of security implies that when business are evaluating SD-WAN options they require to consider the capability of that option to offer both reliable access to cloud resources and effective security. For instance, the SD-WAN option must support functionality such as end-to-end micro-segmentation. Because it isn’t possible for an SD-WAN vendor to supply all the required security functionality, an essential element of a secure SD-WAN option is that the service incorporates with the broadest selection of security suppliers. The service must likewise be capable of identifying, classifying and guiding applications based upon security policies and combine that ability with the ability to service chain to either next generation security infrastructure or cloud-based security services.

Leave a Reply